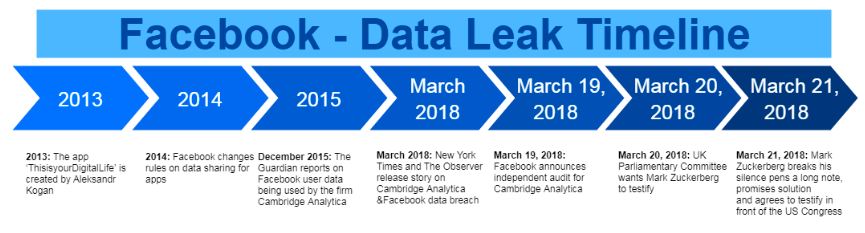
Your job description could be one place to start on Tinder!

The days of being embarrassed about online dating are long gone. It is now a regular occurrence and something people openly talk about in today’s world. Some of this change has been down to how we use the internet and how it is firmly integrated into our lives through work, smartphones & social media. With the growth of online dating platforms comes a growth in the vast collection of profile data. By using our data, these applications are able to provide better matches which lead to more interesting dates and higher chance of compatibility.
So how exactly do dating apps use ‘BIG data’?
1. Multiple data sources:
Many dating apps/sites ask users to fill out questionnaires to gauge user personality and interests as this information is used to generate compatible matches. They then obtain user permission to gather more data through social media platforms, online shopping histories, streaming sites among many others. This is known as ‘collaborative filtering’ as matches users based on factors like the shows they watch & products they buy. E-Harmony uses a proprietary questionnaire with 258 questions which takes approximately 18 hours to complete, contrary to belief this is obviously working as they publicly announced to be responsible for the marriage of 600,000 couples.
2. Deep Learning:
This is probably the creepiest method used by dating & marriage services such as ‘best-matchmaking.com’ & ‘Badoo’ where users are offered the ability to find a partner that resembles another person by analyzing images to identify specific features such as the shape of the nose or colour of the eyes without being mentioned.
3. Analyzing User Behaviour:
This method helps in deciphering what type of partner a particular user is interested in finding. This is done through using the data from the questionnaire, third party data & algorithms to decipher the behavior of the user. This has originated from contradictory user activities where the sort of partner users say they prefer and the sort of profiles they spend most time looking at differs. For example, ‘E-harmony’ uses information such as the frequency of user log ins and amount of time spent on the site to ascertain how serious a user is in finding a partner.
4. Online Dating in Action:
After the user signs for the site/app, data is continuously collected and then analyzed. This data then gets stored in a database and gets linked accordingly with numerous algorithms so the matches are completely automated and provide the best potential matches. This algorithm is unique to each site. One such example is Tinder, with over 50 million users this app is ahead of all the other competition and uses a unique algorithm linked with location, number of mutual friends and common interests and does not use lengthy questionnaires.
Curious about what kind of data Tinder uses from your personal sources? Look no further- https://account.gotinder.com/request-data
References
https://www.makeuseof.com/tag/online-dating-data/
https://medium.com/personaldata-io/tinder-must-be-joking-with-their-dowload-your-data-option-88fdd7b3950d
https://dataconomy.com/2016/02/can-big-data-save-your-love-life/
https://dailydatanews.com/2017/12/01/big-data-dating/
http://www.quantmarketing.com/news/putting-the-big-data-in-dating/
https://www.bmmagazine.co.uk/business/online-dating-is-using-big-data-to-find-compatible-matches/